Reducing complexity, in an authentication method, provides a technical improvement over conventional authentication methods. Applicant’s specification emphasizes the inventive nature of these steps and describes how authentication complexity is reduced.
CosmoKey’s U.S. Patent No. 9,246,903 was found to be ineligible under 35 U.S.C. 101 by a District Court.
The patent is titled “Authentication Method” and discloses an authentication method that is both low in complexity and high in security.
The patent specification indicates that when a user communicates with a remote transaction partner (e.g., a bank, a store, or a secured database) via the Internet, “it is important to assure that an individual that identifies itself as an authorized user is actually the person it alleges to be.” The specification also describes several conventional authentication methods involving a user’s mobile phone.
The specification purports to improve on conventional mobile phone authentication methods in that the “authentication function is normally inactive and is activated by the user only preliminarily for the transaction, said response from the second communication channel includes the information that the authentication is active, and the authentication function is automatically deactivated.” “In this method, the complexity of the authentication function can be reduced significantly” because all that is required “from the authentication function is to permit the authentication device to detect whether or not this function is active” and “the only activity that is required from the user for authentication purposes is to activate the authentication function [within] a suitable timing.” The authentication function is activated within a certain (preferably short) time window after the transmission of the user identification. Since the authentication function is normally inactive, the authentication will almost certainly fail when a third party fraudulently identifies itself as the user in order to initiate a transaction. Then, the authentication would be successful only in the very unlikely event that the true user happens to activate the authentication function of his mobile device just in the right moment. Even in this unlikely case the fraud could be detected. Thus, notwithstanding the low complexity, the method according to the invention offers a high level of security.
Claim 1 is the sole independent claim of the patent and recites:
1. A method of authenticating a user to a transaction at a terminal, comprising the steps of:
- transmitting a user identification from the terminal to a transaction partner via a first communication channel,
- providing an authentication step in which an authentication device uses a second communication channel for checking an authentication function that is implemented in a mobile device of the user,
- as a criterion for deciding whether the authentication to the transaction shall be granted or denied, having the authentication device check whether a predetermined time relation exists between the transmission of the user identification and a response from the second communication channel,
- ensuring that the authentication function is normally inactive and is activated by the user only preliminarily for the transaction,
- ensuring that said response from the second communication channel includes information that the authentication function is active, and
- thereafter ensuring that the authentication function is automatically deactivated.
Under Alice step one, the Federal Circuit considered “what the patent asserts to be the `focus of the claimed advance over the prior art.'” The district court held that the claims “are directed to the abstract idea of authentication —that is, the verification of identity to permit access to transactions.” The Federal Circuit was not convinced that this broad characterization of the focus of the claimed advance is correct. Rather, the claims and written description suggest that the focus of the claimed advance is activation of the authentication function, communication of the activation within a predetermined time, and automatic deactivation of the authentication function, such that the invention provides enhanced security and low complexity with minimal user input. The critical question then is whether this correct characterization of what the claims are directed to is either an abstract idea or a specific improvement in computer verification and authentication techniques.
The Federal Circuit stated that they need not answer this question, however, because even if they accepted the district court’s narrow characterization of the patent claims, the claims satisfy Alice step two.
The patent claims and specification recite a specific improvement to authentication that increases security, prevents unauthorized access by a third party, is easily implemented, and can advantageously be carried out with mobile devices of low complexity. Contrary to the district court’s conclusion, the patent discloses a technical solution to a security problem in networks and computers. While authentication of a user’s identity using two communication channels and a mobile phone was known at the time of the invention, nothing in the specification or anywhere else in the record supports the district court’s suggestion that the last four claim steps—including (1) “as a criterion for deciding whether the authentication to the transaction shall be granted or denied, having the authentication device check whether a predetermined time relation exists between the transmission of the user identification and a response from the second communication channel”; (2) “ensuring that the authentication function is normally inactive and is activated by the user only preliminarily for the transaction”; followed by (3) “ensuring that said response from the second communication channel includes information that the authentication function is active”; and (4) “thereafter ensuring that the authentication function is automatically deactivated,” are conventional.
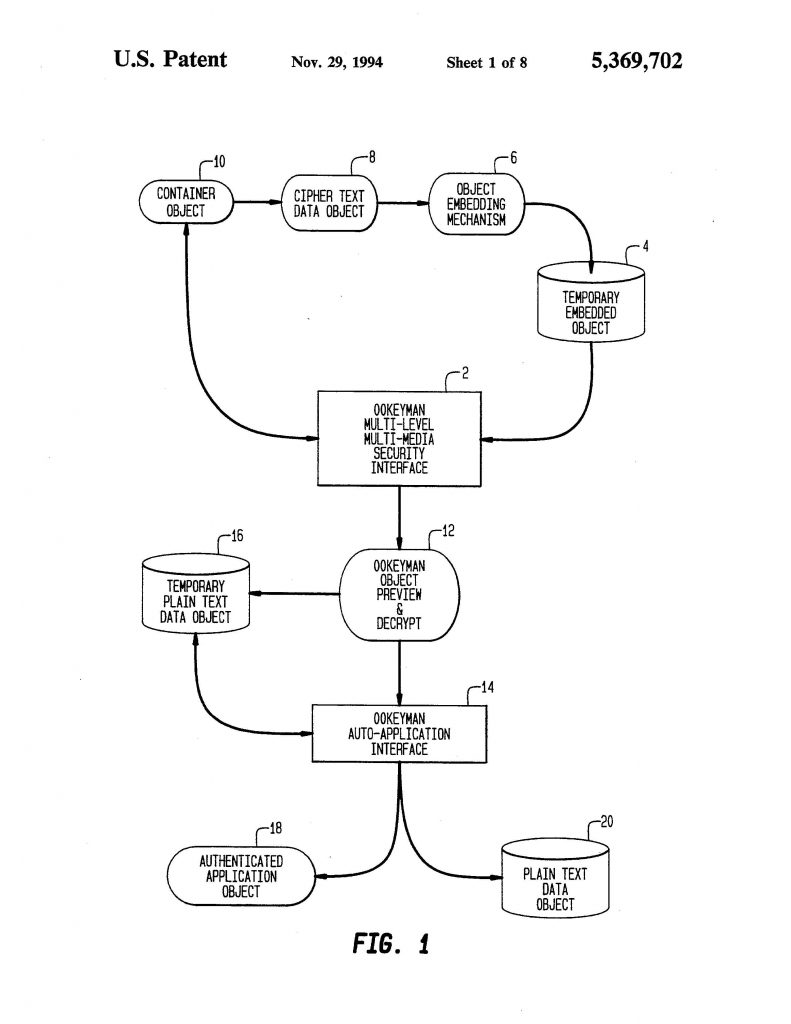 Multilevel security claims were patent eligible because they were directed to solving a technical problem specific to computer network security. The district court correctly rejected Adobe’s ineligibility challenge.
Multilevel security claims were patent eligible because they were directed to solving a technical problem specific to computer network security. The district court correctly rejected Adobe’s ineligibility challenge. Even patent applications covering mechanical inventions can be invalidated using the same
Even patent applications covering mechanical inventions can be invalidated using the same 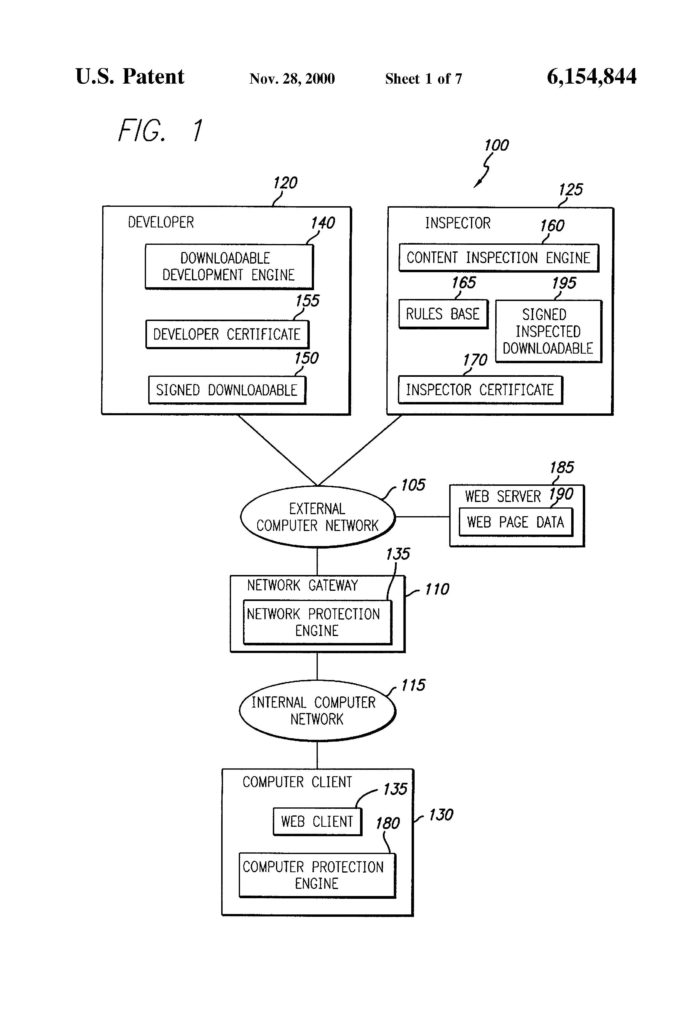 Finjan brought suit against Blue Coat for infringement of software patents directed to identifying and protecting against malware. One of the software patents is directed to a method of providing computer security by scanning a downloadable and attaching the results of that scan to the downloadable itself in the form of a “security profile.”
Finjan brought suit against Blue Coat for infringement of software patents directed to identifying and protecting against malware. One of the software patents is directed to a method of providing computer security by scanning a downloadable and attaching the results of that scan to the downloadable itself in the form of a “security profile.”